M3.4: Final Research Artifact
Research Status: COMPLETE
Section titled “Research Status: COMPLETE”Date: January 2026 Version: M3.4-final (Gold Master)
This log marks the conclusion of the active engineering phase. Sentinel Runtime has transitioned from a development prototype to a validated Research Artifact for the CISPA MSc Application.
The Release Package
Section titled “The Release Package”- Codebase: Clean separation of concerns (
src/vstests/). - Defense: Full coverage for Ransomware, Exfiltration, and Rootkits.
- Resilience: New Watchdog Orchestrator (
scripts/watchdog.sh) ensures the defense cannot be disabled viaSIGKILL.
Performance Benchmark (Final)
Section titled “Performance Benchmark (Final)”We conducted a final stress test to quantify the cost of “Active Defense.”
| Metric | Result | Context |
|---|---|---|
| Syscall Latency | ~30x overhead | Unavoidable with ptrace. Acceptable for high-security modes. |
| IPC Throughput | 28,628 events/sec | Sufficient for standard desktop workloads. |
| Memory Usage | 110 MB | Stable (Python Runtime + TensorFlow Lite). |
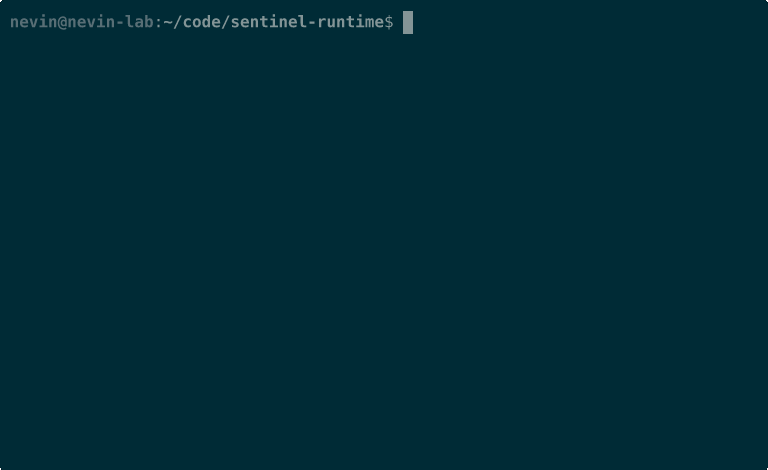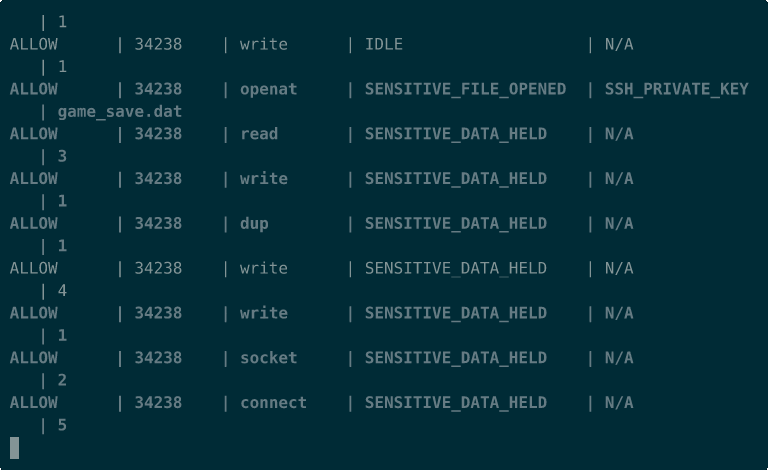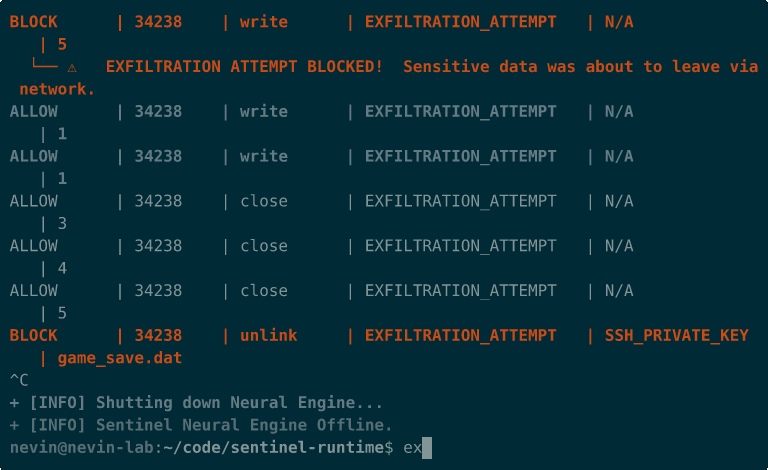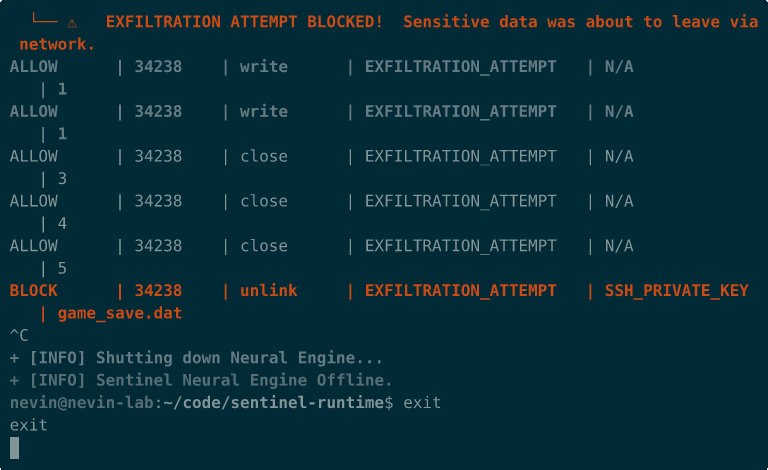
Evidence of Defense
Section titled “Evidence of Defense”The following immutable artifacts verify the system’s efficacy.
Sentinel Active Defense Demo:
- Ransomware Block: Immediate termination of encryption loop.
- Exfiltration Block: Detection of tainted data leak.
- Persistence: Automatic resurrection after
kill -9.